6. Code quality. Code Style. Liters. Static code analysis. PHP Insights.
Video version
(Leave your feedback on YouTube)
Use Static Code Analysis, Linters, Code formatter
Nothing will improve the quality of your code and the speed of code reviews like using automated tools for code styling. As a bonus, you'll catch errors/bugs at an early stage.
Review the solutions, not the code style.
Very often, teams implement code style rules "verbally". They send each other links to standards and spend a lot of time on checking and conflicts during reviews, which are never perfect.
So please spend at most a couple of hours at the beginning of development, or a few weekends on an ongoing project, to set up a code formatter or linter. Be sure to add checks on pre-commit and as a step in CI/CD.
For PHP and Laravel specifically, I recommend taking a look at PHP Insights. This solution is a combination of a static code analyzer and a linter with an additional bonus—analysis of vulnerabilities in composer dependencies and a metric for cyclomatic complexity of the code.
And another small bonus of Insights is the "user-friendly" display of analysis results. Of course, it is not necessary, but sometimes it is useful show green squares with the inscription 100% to the customer.
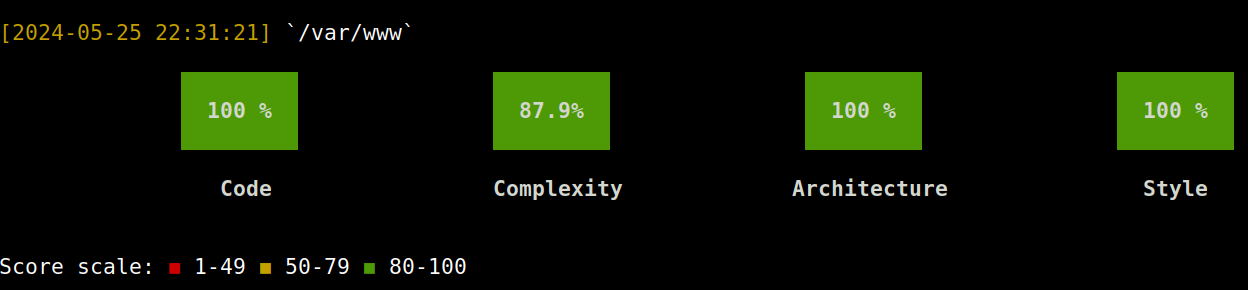
PHP Insights is not the only option that can easily be used with other solutions like PHP_CodeSniffer, Psalm, PHPMD etc. Look for ready-made collections with rules, it will be much faster.
Expect that the first few months of development the ruleset will be actively changed by the team, feel free to customize them to your needs.
Pay attention to:
'requirements' => [
'min-quality' => 100,
'min-complexity' => 85,
'min-architecture' => 100,
'min-style' => 100,
'disable-security-check' => false,
],
min-quality, min-architecture, min-style - always set 100. It makes no practical sense to give leeway to violations
some rules. Better customize the rules here.
min-complexity - Do not set below 80. You will notice that it is bad code that lowers this indicator, and "bad smelling" scripts
php insights will highlight.
'disable-security-check' => false - You should never turn off the security check.
Insight automatically scans your dependencies and checks against a database of known vulnerabilities.
The check will not pass if any of your dependencies have a vulnerability and that's very cool!
It will be perfect to run this check even on a schedule for projects in prod.
Usually, the community reacts quickly to found vulnerabilities, and fixes take no more than 12 hours. Just waiting (or helping) when it is fixed,
do composer update and live peacefully.
Security testing is important! Keep it enabled in PHPInsight or configure your own.
You should also know that you can disable any code style rule for a file or a specific line:
/**
* @phpcsSuppress SlevomatCodingStandard.Functions.UnusedParameter
*/
$someUnusedParameter
Don't forget to add a pre commit hook
docker exec -t bh-app php artisan insights --fix --no-interaction
git add $(git diff --cached --name-only --diff-filter=ACM)
docker exec -t bh-app php artisan insights --fix --no-interaction- fix the code immediately with verification. It is very useful does not force developers to think about code style at all.git add $(git diff --cached --name-only --diff-filter=ACM)- add all the files that were already in the index to the index again. It is necessary that autocorrections were added to the commit without developer intervention
Add a check as a CI/CD step.
stages:
- test
default:
image: docker:26.1.3-alpine3.19
services:
- docker:26.1.3-dind
insights:
stage: test
before_script:
- cp .env.example .env
- echo UID=$(id -u) >> .env
- echo GID=$(id -g) >> .env
- docker login -u $CI_REGISTRY_USER -p $CI_REGISTRY_PASSWORD $CI_REGISTRY
- docker compose up app -d --no-deps
- docker compose exec app composer install --no-scripts
script:
- docker compose exec app php artisan insights --no-interaction
Pay attention:
docker login -u $CI_REGISTRY_USER -p $CI_REGISTRY_PASSWORD $CI_REGISTRY- authorization to access the app container. Required for the project with docker container go toSettings=>CI/CD=>Token Access=>Limit access to this project.Add group or projectadd name of current project or group (subgroup).docker compose up app -d --no-deps- run onlyappcontainer, without dependencies (depends_on)